Trustless Custody helps you protect your digital assets like cryptocurrency private keys, passwords, and documents (“secrets”) from malice, theft, hackers, accident, and disaster without needing to trust any single party. A TC vault makes it easy to safely store and backup your digital assets and enables them to be safely passed on to your heirs.
A Trustless Custody vault comes on an easy-to-use, secure, encrypted laptop. You can store your crypto assets, critical documents, and other secrets in your vault by dragging-and-dropping files just like any other folder. The password to open this vault is known only to you, and nobody can get in without the password. Because the vault cannot be opened without the password, you can safely store backups of the vault without needing to trust the parties you give copies to. Want more technical details? See our Technical FAQ.
For your safety and ours, we never have access to your secrets or even know what they are. Our job is to help you (and your heirs) use battle-tested cryptographic solutions to protect and disperse your secrets under conditions you choose. These are the same cryptographic solutions used by Fortune 500 companies to protect their most important intellectual property such as secret formulas.
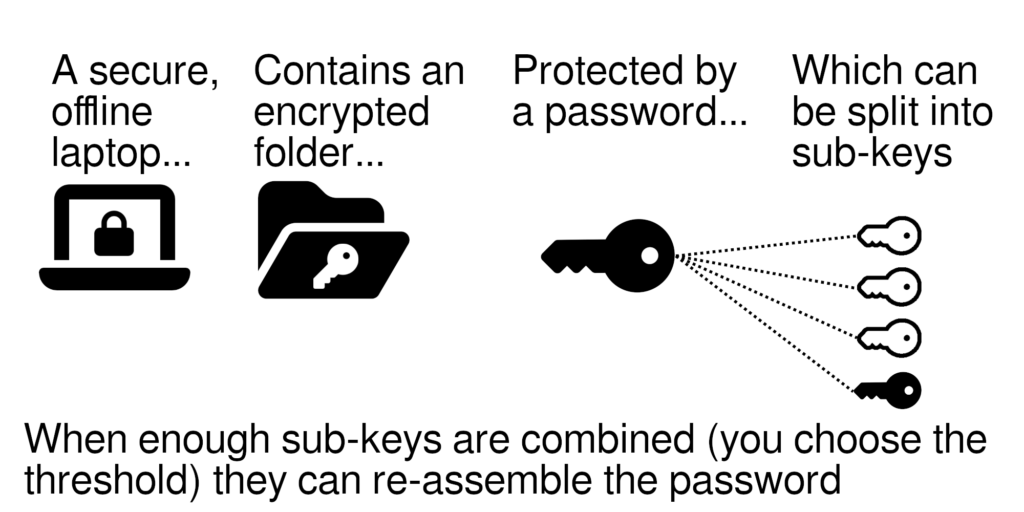
A TC vault is stored on a secure, offline laptop enhanced with the latest security settings and application. It also has a magic encrypted folder (vault). The vault is easy to use and backup: simply drag & drop files into it like you would any other folder. Being on a small laptop, this makes your vault portable. And since it’s easy to backup (and encrypted), you can safely store backups with other parties without having to trust them.
The laptop comes pre-installed with wallets for the most popular cryptos, so you can easily generate offline (cold storage) wallets and sign transactions offline.
Being offline helps protect against many different attacks. We can setup this system for you remotely (most popular) or in person for those requiring additional discretion. Importantly, Trustless Custody never has access to your data or keys. This system is fully self-custody.
The data in the vault is encrypted using battle-tested cryptography which is safe against even quantum computing attacks. This vault is protected by your passphrase. The encryption would take millions of years to crack, nobody is getting in!
Because the vault works just like a regular folder, you can store any kind of file in it: crypto wallets, documents, photos, anything you’d like!
The encrypted folder (vault) is all stored inside a single file. This means you can easily transfer the entire vault onto flash drives or external hard drives to make backups. And because they are encrypted, you can safely store these backups without needing to trust the storage provider (such as Google Drive).
All of this security is designed to be easy to use, so you only need to remember a single password to protect all your data.
We can also split your password into “sub-keys”, which enable you to recover your password in the event you lose or forget it, and can also be used by your heirs to access the vault if something were to happen to you. You choose how many keys are created, who they are given to, and how many must be combined to rebuild the original password (threshold). Want 3/5 of your heirs? No problem! How about your lawyer, your banker, and one of your heirs? Absolutely! If somebody doesn’t have the correct number of sub-keys, they cannot re-assemble your passphrase.
Holders of your sub-keys receive:
– An electronic copy of the keys on a flash drive
– A paper copy of the keys, as paper is best for long-term storage
– Step-by-step directions for using their sub-keys to open the vault
Get Started
- You schedule a free online or phone consultation with us. We’ll answer all your questions so you can decide if a TC vault is the right solution for you.
- We setup a system for you at the time and place of your choosing (online or in-person in Oregon). Your secrets are placed onto an encrypted storage device, and keys are distributed to whomever needs them. Your system comes with step-by-step directions for re-assembling the secrets.
- Our services are billed on a flat-rate basis, so you’ll know the full cost before you commit to anything